How do you connect to a Linux server? SSH stands for Secure Shell, and it’s the recommended way of connecting to a remote host. SSH uses an encrypted protocol that allows you to create a remote connection through an SSH tunnel until you disconnect.
Whether you are new to or experienced with SSH, you should understand what SSH keys are and how to utilize them to add an additional security layer. Thankfully, this post focuses on configuring SSH key-based authentication on a Linux server. We will understand SSH keys, how they work, and how to configure them. Ready? Let’s get started!
Configuring SSH Key-Based Authentication
For SSH to establish a connection between a client and a server, a form of authentication must be used. In most cases, SSH authentication is based on passwords. However, there are other ways to authenticate. Although SSH is a secure protocol, password-based authentication creates a risk of brute-force attacks that can eventually break into your server.
Turning off password authentication and using SSH key pairs instead is recommended. The SSH key pairs consist of public and private cryptographic keys. The private key is held by the client device, while the remote host holds the public key. The private key is the most important and should be held securely. If compromised, the private key will give access to your server.
When establishing a remote connection via SSH, the server checks its public key to see if it matches the provided key. The connection will be established, and no password will be required to authenticate the client.
Let’s go through the steps to configure SSH key-based authentication.
Step 1. Generating the SSH Key Pairs
We’ve already discussed public and private keys. The first step in configuring SSH-key-based authentication is to generate the SSH keys on your client device. The private key will remain secured on your client, while the public key will be copied to the remote host.
SSH provides the ssh-keygen to help with generating the keys. By default, ssh-keygen uses RSA to generate a 3072-bit key pair using the below command.
When you run the command, you will be prompted to choose where to save it. You can specify a different location or press the enter key to save it in the specified location.
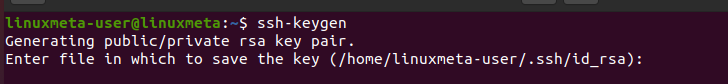
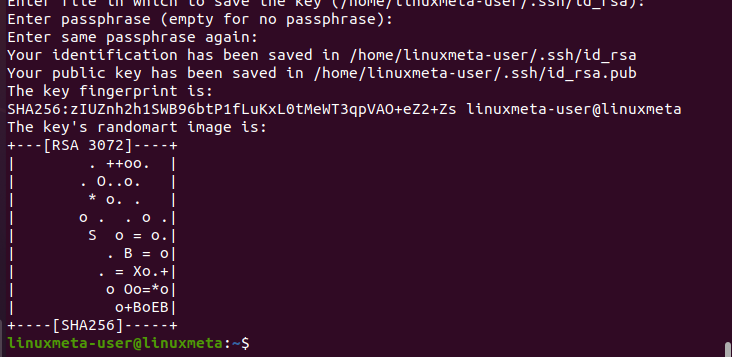
Next, you will be prompted whether to add a passphrase. If added, you must type it when establishing the connection. As such, the passphrase acts as another security layer on top of the SSH keys.
Lastly, the SSH keys will be generated, and you will get an output confirming this, including an image representing the generated key fingerprint.
Step 2: Copy the Generated SSH Public Key to the Linux Server
Once the SSH keys are generated, store the private key securely. Consider encrypting the disk to ensure nobody can access it. We must copy the public key to the server.
Although there are various ways to copy the key, this post will focus on the ssh-copy-id. It is the simplest option, and the tool is included in every OpenSSH installation.
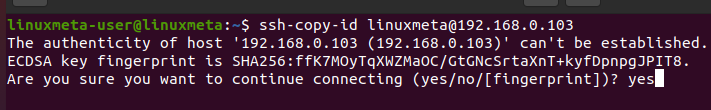
To use it, ensure you have your server’s IP and the username of the client you want to connect to on your server. With that, you can run the following command.
Since we are connecting to the server for the first time via SSH, we will get prompted to confirm the fingerprint. Type ‘yes’ and hit the enter key.
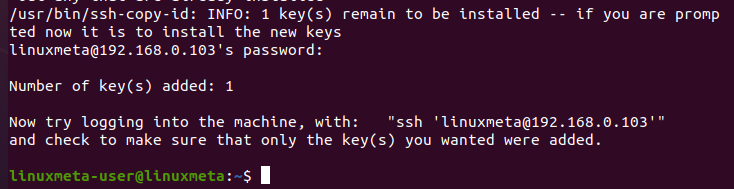
You must then authenticate using the credentials for the user account. Once you enter the password, you will see an output that the SSH public key has been added. That’s all you need to do.
Step 3: Verify the SSH Key-Based Authentication
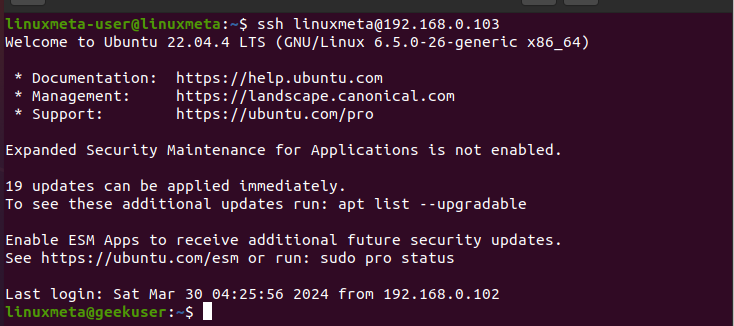
For this step, we must confirm that we can now access our Linux server without a password. To do so, create the SSH connection using the following syntax.
If you aren’t prompted to enter your password but manage to log in, this confirms that our SSH key-based authentication works.
Step 4: Disable Password Authentication on the Linux Server
Although we’ve managed to set up the key-based authentication, we are still at risk of a brute-force attack unless we disable password authentication.
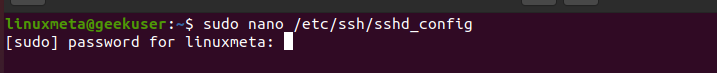
Here’s what you should do: access your Linux server and open the sshd_config file.
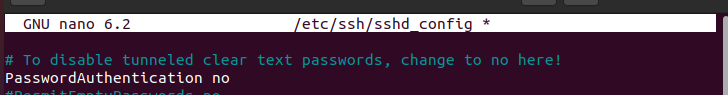
Access the PasswordAuthentication line on the file and set it to ‘no’ as in the image below.
Save the changes on the file and close the text editor.
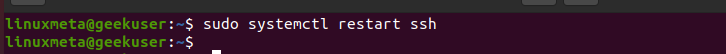
You then must restart SSH.
Conclusion
SSH is a secure way of connecting to a Linux server. However, setting up SSH key-based authentication adds more security. This post elaborates on every step you should follow to effectively configure SSH key-based authentication on a Linux server. All the best!